Phishing is not new, but it’s evolving faster than most defenses. From inboxes to smartphones to collaboration apps, attackers are finding new ways to exploit human trust. According to industry data, phishing is the leading cause of cyber breaches worldwide, with more than 3.4 billion fake emails sent every day.
So why does phishing remain so successful? The answer lies in psychology. Unlike malware that breaks in through code, phishing walks in through persuasion. If your employees don’t know how to spot it, no firewall or antivirus can fully protect you.
This guide will break down exactly how phishing works, why it’s so effective, and what steps you can take to protect your team. Along the way, we’ll pose a few questions you can use to spark internal discussions and training exercises.
Understanding Phishing: The Digital Confidence Game
At its core, phishing is a digital con game. Cybercriminals impersonate trusted individuals or organizations to trick victims into revealing sensitive information, transferring money, or granting access to systems.
The UK’s National Cyber Security Centre explains phishing as a method of gathering personal information through deceptive communications. Unlike a brute-force attack, phishing leverages credibility, urgency, and familiarity — the same principles used by con artists for centuries.
👉 Ask yourself: Would every member of your team know the difference between a legitimate company email and a carefully crafted fake one?
The Psychology and Mechanics of a Phishing Attack
Phishing works because it preys on universal human instincts: fear of missing out, urgency, trust in authority, and desire for rewards.
A typical phishing campaign follows this playbook:
- Preparation – Attackers register look-alike domains or compromise legitimate email accounts.
- Delivery – The lure arrives via email, SMS, phone, or even messaging apps like Slack or Teams.
- Deception – The message creates urgency (“Your account will be suspended today”), authority (“HR has sent you a document to sign”), or opportunity (“Click here for a bonus reward”).
- Engagement – Victims click the link, download a file, or enter credentials on a spoofed site.
- Exploitation – The stolen data or access is sold, used for fraud, or leveraged in larger attacks like ransomware.
The CrowdStrike guide on phishing emphasizes that phishing bypasses even advanced defenses because it targets behavior. One click is often enough to compromise an entire network.
👉 Training exercise idea: Share an example of a suspicious email with your team. Ask: “Which elements look off to you?”
The Many Faces of Phishing Attacks
Phishing isn’t one-size-fits-all. Criminals tailor their attacks to maximize success rates. Common variations include:
- Mass Email Phishing – Spray-and-pray attacks that target thousands of recipients at once.
- Spear Phishing – Personalized messages that reference specific projects, colleagues, or industries.
- Whaling – High-value targeting of executives, board members, or finance officers.
- Smishing & Vishing – Attacks through SMS and voice calls, often impersonating banks or government agencies.
- Clone Phishing – A legitimate email is copied and altered with a malicious link or attachment.
The Gotyto blog highlights how each of these types requires different defensive strategies — there’s no single “silver bullet.”
👉 Ask yourself: Which type of phishing would most likely succeed against your organization today?
Why Phishing Is So Damaging for Businesses
Phishing attacks don’t just lead to stolen passwords — they ripple through entire organizations:
- Financial Losses – Fraudulent wire transfers or stolen payment details.
- Data Breaches – Exposure of confidential customer or employee information.
- Reputational Harm – Customers lose trust when they learn of a breach.
- Regulatory Penalties – Violations of GDPR, HIPAA, or PCI compliance rules.
- Operational Downtime – IT teams scramble to investigate and recover, slowing business.
One well-documented phishing attack involved a multinational company that lost over $100 million after attackers impersonated a vendor and tricked employees into wiring funds. All it took was one employee falling for one convincing email.
👉 Discussion prompt: What would be the financial and reputational cost if one of your team members accidentally exposed sensitive data?
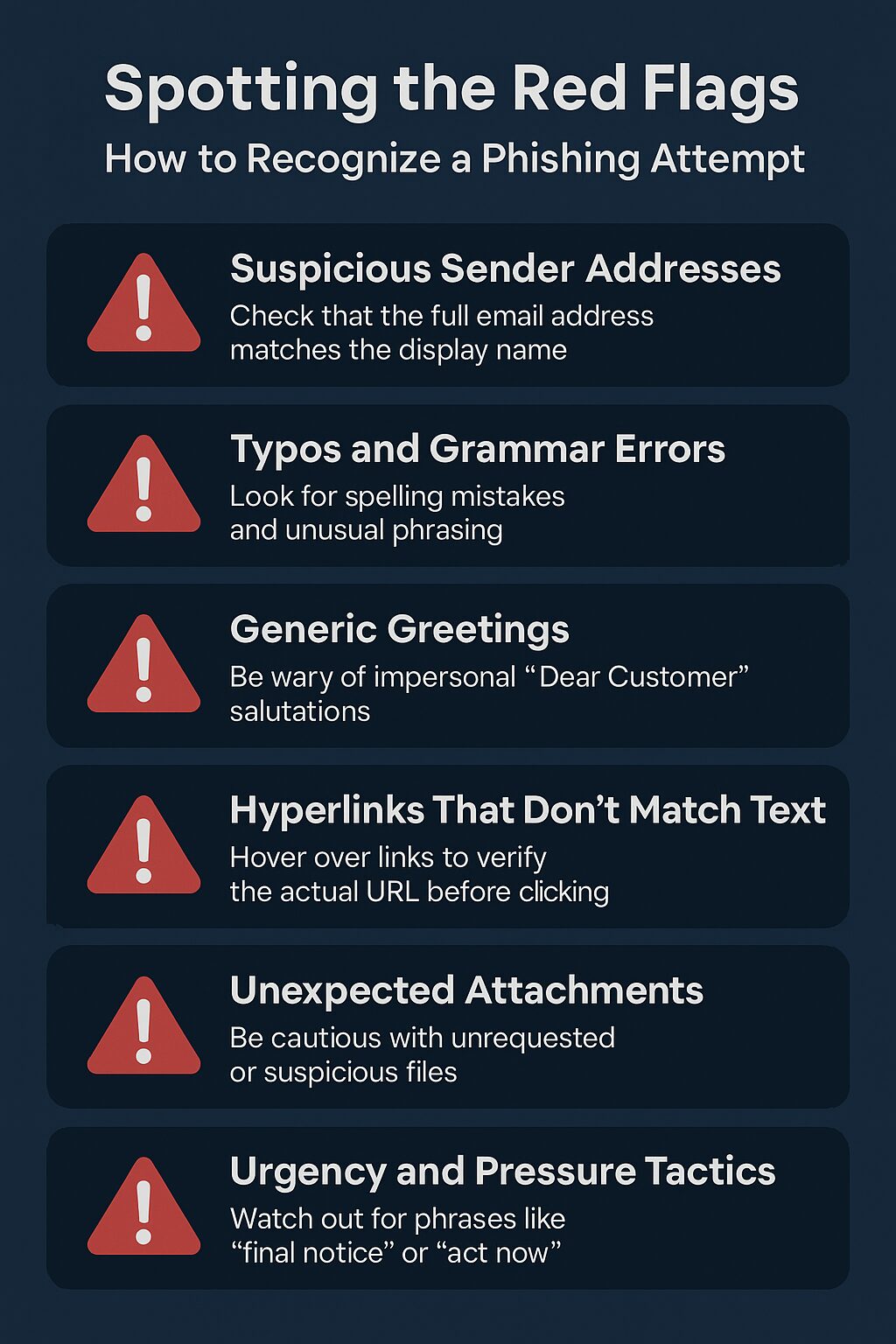
Spotting the Red Flags: How to Recognize a Phishing Attempt
As phishing emails grow increasingly convincing, it’s easy to be fooled if you’re not looking closely. However, attackers often leave behind small but telling clues. Training your team to spot these red flags can dramatically reduce your risk of falling victim. Let’s break them down in detail:
Suspicious Sender Addresses
Attackers often use display names that look legitimate, but the actual email address tells a different story. For example, an email may appear to come from “Microsoft Support,” but the underlying address might be something like support@m1crosoft-security.com. The extra character, odd spelling, or unfamiliar domain are all giveaways.
👉 Tip: Always check the full sender address, not just the display name.
Typos, Grammar Errors, and Awkward Phrasing
While professional-looking emails are becoming more common, many phishing messages still contain unusual phrasing, spelling mistakes, or grammar errors. This happens because attackers may not be fluent in the target’s language or may deliberately insert errors to filter out more cautious recipients.
👉 Example: “Your account has been suspended. Please verify immediately.”
Generic Greetings Instead of Personalization
Legitimate organizations usually personalize their communications with your name or account information. Phishing emails, especially mass campaigns, often use vague greetings like “Dear Customer” or “Dear User.”
👉 Red flag: If your bank knows your name when you log in, why wouldn’t they use it in an official email?
Hyperlinks That Don’t Match Their Text
One of the most common tricks is hiding malicious links behind legitimate-looking text. For example, a link may read www.paypal.com, but hovering over it reveals a completely different domain like www.paypalsecure-login.biz.
👉 Tip: Hover your mouse over links before clicking to verify the true destination. On mobile devices, press and hold the link to preview it.
Unexpected Attachments
Unsolicited files, especially compressed files (.zip, .rar) or executables (.exe, .bat), are a classic phishing tactic. These attachments often contain malware designed to install silently when opened. Even seemingly harmless file types like PDFs or Word documents can be weaponized with malicious macros.
👉 Rule of thumb: If you weren’t expecting an attachment, treat it with suspicion. Confirm with the sender through another channel before opening.
Urgency and Pressure Tactics
Phishing often relies on creating a sense of panic or urgency to short-circuit rational decision-making. Messages may threaten to suspend your account, close your access, or miss out on a reward if you don’t act immediately.
👉 Example phrases:
- “Final Notice: Your account will be closed in 24 hours.”
- “Immediate action required to avoid penalties.”
- “Click here to secure your account now.”
Legitimate organizations rarely demand instant action without giving you a chance to verify through official channels.
The FTC’s phishing prevention tips are a great resource to share with employees.
👉 Training idea: Create a “spot the scam” challenge once a month by sending employees real-world examples to analyze.
Building a Strong Defense Against Phishing
Protecting your team means combining people, processes, and technology into a layered defense.
Empower Through Education
Run regular awareness training sessions and simulated phishing campaigns. Encourage employees to report suspicious messages rather than ignore them.
Deploy Technical Safeguards
- Email Filtering – Block or quarantine suspicious communications.
- Multi-Factor Authentication (MFA) – Adds a second line of defense even if passwords are stolen.
- Endpoint Detection & Response (EDR) – Monitors for malicious activity on devices.
Create Clear Policies and Procedures
- Establish a simple reporting channel for suspicious emails.
- Enforce the principle of least privilege — limit access to only what’s necessary.
- Keep software and systems updated to minimize exploitation.
Resources like Lift HCM’s phishing protection strategies and Splashtop’s 10 employee prevention tips provide actionable steps you can start implementing immediately.
👉 Ask yourself: Does your team know exactly what to do the moment they suspect an email might be phishing?
Responding Effectively If an Attack Succeeds
No defense is perfect. If someone in your organization falls victim to phishing:
- Disconnect the device from the network.
- Reset passwords immediately for any affected accounts.
- Notify IT/security teams and provide details of the attack.
- Scan for malware to ensure no secondary infections.
- Inform stakeholders if required (customers, regulators, partners).
Having a rehearsed incident response plan reduces panic and limits the damage.
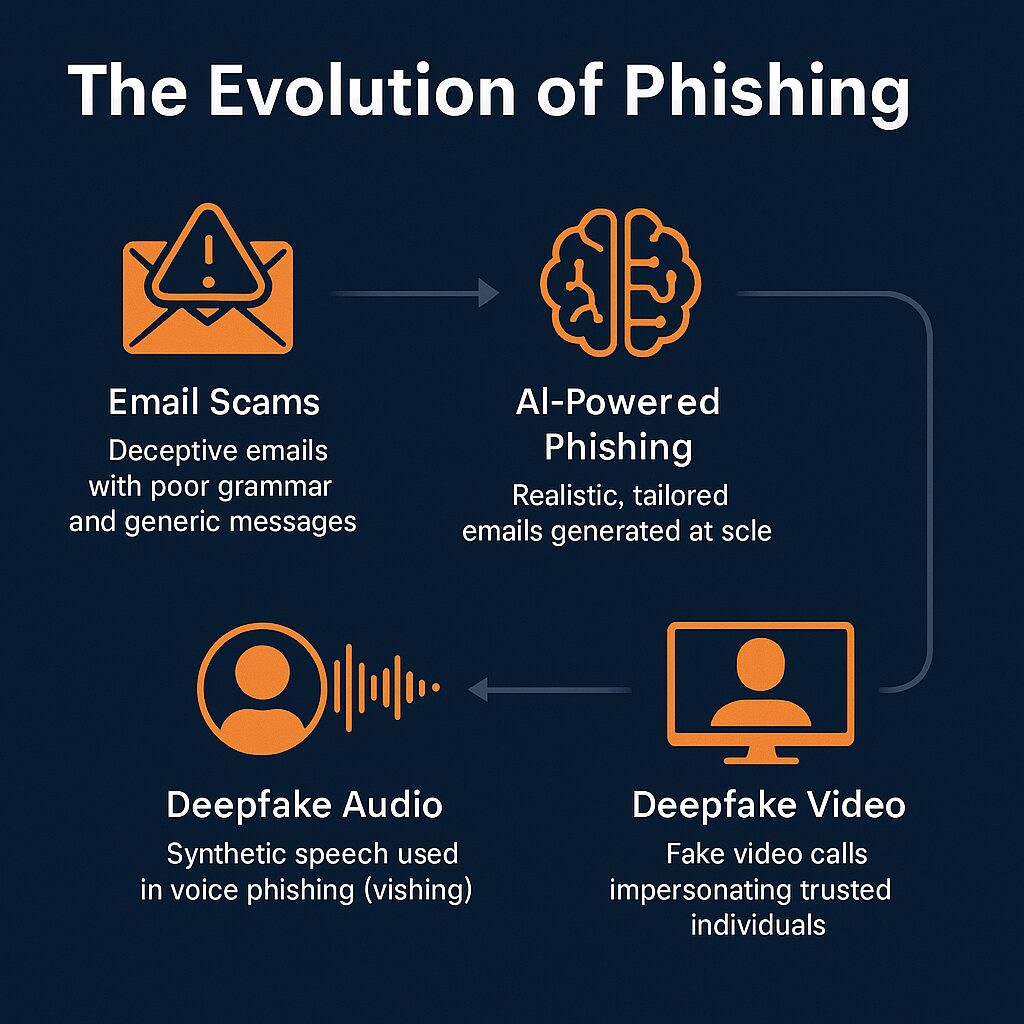
The Future of Phishing: AI-Driven Attacks and Deepfake Deception
Phishing is no longer limited to clumsy emails filled with typos and broken links. Attackers are harnessing advanced technologies like artificial intelligence (AI) and deepfake media to create more sophisticated, convincing, and harder-to-detect scams. This evolution makes phishing one of the most pressing cybersecurity challenges of the next decade.
AI-Powered Phishing Campaigns
Cybercriminals are increasingly using AI to:
- Generate convincing messages at scale – Tools like large language models allow attackers to instantly create thousands of polished, grammatically correct phishing emails in any language, customized to industry jargon or local context.
- Personalize attacks through data mining – AI can scrape LinkedIn, social media, and corporate websites to craft highly tailored spear-phishing messages that reference specific projects, colleagues, or events.
- Bypass detection systems – AI can tweak emails slightly each time they’re sent, making it harder for traditional spam filters to block them.
👉 Example: Instead of a generic “reset your password” email, an AI-driven phishing attack could reference a recent company event, include the names of actual executives, and imitate the exact tone of your internal communications.
Deepfakes and Voice Phishing (Vishing)
Even more alarming is the rise of deepfake technology — synthetic media that can convincingly replicate someone’s appearance, voice, or mannerisms.
- Deepfake audio has already been used in real attacks, tricking employees into transferring funds after receiving what sounded like instructions from their CEO.
- Deepfake video could allow attackers to appear on a Zoom or Teams call as a trusted executive or partner, instructing teams to take urgent (but fraudulent) actions.
👉 Imagine this scenario: You receive a voicemail from your CFO confirming a last-minute vendor payment. The voice matches perfectly — but it was generated by a cybercriminal using just a few minutes of recorded audio found online.
Blurring the Line Between Real and Fake
The future of phishing is dangerous because it attacks not just technology but our perception of reality. As deepfakes improve, distinguishing real from fake will become increasingly difficult. This means employees can no longer rely solely on instinct or recognition — they’ll need verification processes for sensitive requests.
Defending Against Emerging Phishing Threats
While the threat is evolving, so are defenses. Organizations can prepare by:
- Implementing verification protocols – Require multi-step verification for financial transactions or sensitive data requests (e.g., a secondary confirmation channel, not just email or voice).
- Investing in AI-powered security tools – Advanced detection systems can analyze communication patterns and flag anomalies that suggest impersonation.
- Limiting publicly available data – The less information attackers can scrape online (e.g., executive bios, direct contact info), the harder it is for them to build convincing deepfakes.
- Regular awareness training – Teach employees about emerging threats and emphasize “trust but verify” practices.
- Monitoring developments in regulation – Governments and cybersecurity organizations are developing tools to detect and label synthetic media, but these are still in early stages.
Key Takeaway
The next wave of phishing will be smarter, faster, and harder to recognize. Organizations that rely only on yesterday’s defenses will be outmatched. Success will come from building adaptive defenses that combine human vigilance, advanced security tools, and strong organizational policies.
👉 Ask yourself: If an attacker used AI to impersonate one of your executives tomorrow, how confident are you that your team would recognize — and stop — the scam?
Frequently Asked Questions (FAQs)
What’s the most common type of phishing attack today?
Mass email phishing is still the most common, but spear phishing is far more dangerous because it’s personalized and harder to detect.
Can antivirus software stop phishing attacks?
Not directly. Antivirus helps detect malicious attachments, but phishing primarily exploits human error. Awareness and MFA are stronger defenses.
What’s the difference between phishing and smishing?
Phishing typically occurs through email, while smishing uses SMS/text messages to trick victims.
How often should we run phishing simulations?
Quarterly is a good minimum, though high-risk industries may benefit from monthly tests.
What should employees do if they clicked a phishing link?
Report it immediately, disconnect from the network, and reset their credentials. Early reporting is critical to damage control.
Final Thoughts: Building a Culture of Cyber Awareness
Phishing thrives because it exploits trust, authority, and urgency. The most advanced firewall in the world can’t protect you if one employee clicks on the wrong link. That’s why your ultimate defense is a culture of awareness and resilience.
Invest in training, deploy layered defenses, and ensure your team feels empowered to question suspicious activity. When everyone understands that cybersecurity is a shared responsibility, phishing loses its power.
👉 Final question for you: Is your team prepared to face the next phishing attempt — or will your defenses stop at the inbox?