Why Penetration Testing Matters for Every Organization
Cyberattacks are no longer a distant threat—they’re a daily reality. Organizations of every size are vulnerable, from startups relying on SaaS tools to global enterprises managing massive cloud environments, mobile apps, and complex CI/CD pipelines. According to IBM’s Cost of a Data Breach Report, the global average cost of a breach in 2023 was $4.45 million—a number rising each year.
So how do you know if your defenses can withstand a real-world attack? That’s where penetration testing comes in.
This article breaks down everything you need to know about penetration testing—what it is, how it works, why it matters, how it compares to other approaches, and where it’s heading in the future.
What is a Penetration Test?
A penetration test (or “pen test”) is a simulated cyberattack performed by ethical hackers to uncover security weaknesses. Unlike automated vulnerability scans, penetration tests attempt to exploit vulnerabilities to show the potential real-world impact.
Think of it as a crash test for your IT systems. Instead of guessing how safe your infrastructure is, you put it through a controlled test to see where it would break.
According to IBM, penetration testing provides critical insights into how attackers might move laterally across networks, exploit misconfigurations, or exfiltrate sensitive data.
Why Penetration Testing Matters for Every Organization
Penetration testing isn’t just for highly regulated industries like finance or healthcare—it’s valuable for every business. Here’s why:
- Reduce risk: Identify and fix vulnerabilities before malicious actors find them.
- Prove compliance: Regulations like PCI DSS, HIPAA, ISO 27001, and GDPR often require regular testing.
- Protect reputation: Demonstrating security diligence reassures customers and partners.
- Strengthen defenses: Security teams gain hands-on experience responding to real-world attack simulations.
📌 Think about it: If attackers tested your systems tomorrow, what would they find?
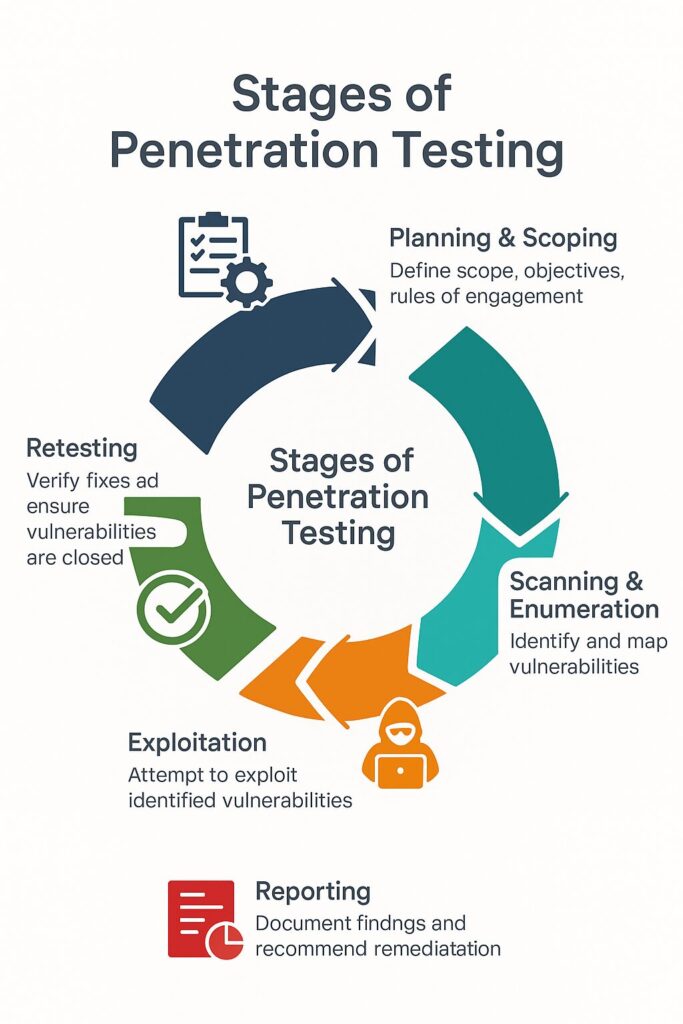
Stages of Penetration Testing
Penetration testing follows a structured process. The five core stages are:
- Planning & Scoping
- Define goals, systems in scope (e.g., web applications, databases, firewalls), and rules of engagement.
- Example: Decide if third-party cloud storage should be included.
- Scanning & Enumeration
- Gather information using tools like Nmap, Burp Suite, and Nessus.
- Map networks, identify open ports, and discover exposed APIs.
- Exploitation
- Attempt to exploit discovered weaknesses.
- Examples: SQL injection in web applications, weak authentication in APIs, insecure firmware in embedded devices (IoT).
- Reporting
- Provide a detailed report with vulnerabilities, exploitation details, risk ratings, and remediation steps.
- Retesting
- After fixes are applied, the tester retests to verify that vulnerabilities are eliminated.
✅ Pro tip: Retesting is often overlooked but is critical to ensure remediation was successful.
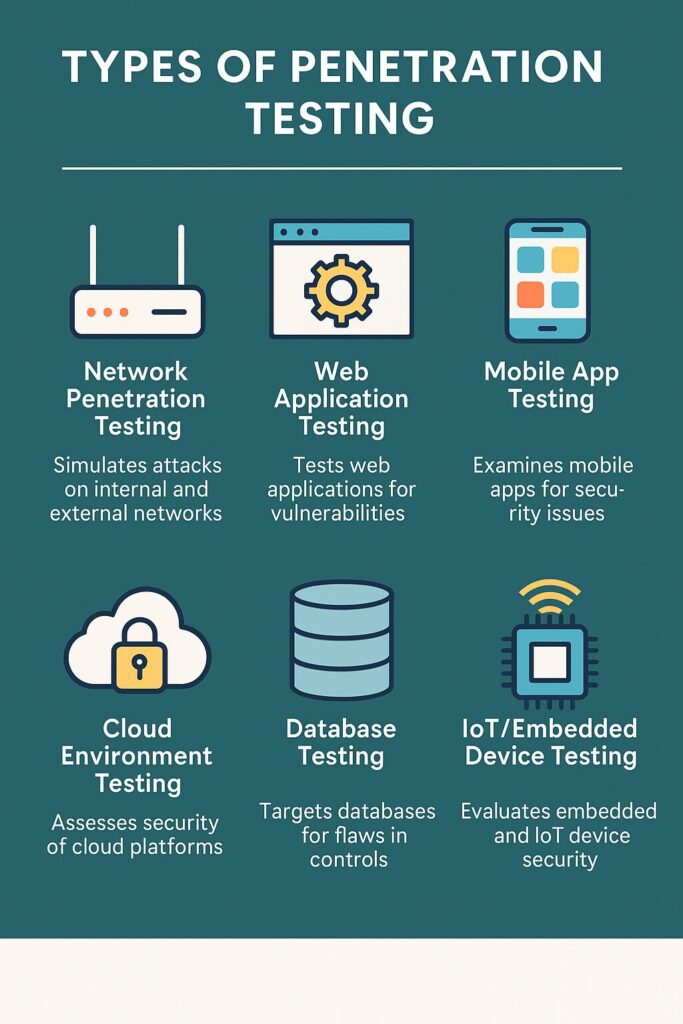
Types of Penetration Testing
Different tests target different parts of your environment:
- Network Penetration Testing – Assess routers, switches, and servers for weaknesses.
- Web Application Testing – Look for injection flaws, XSS, and authentication issues.
- Mobile App Testing – Test for weak encryption, insecure APIs, and poor session handling.
- Cloud Environment Testing – Validate cloud configurations and IAM roles.
- Database Testing – Assess access control, patching, and privilege escalation.
- IoT & Embedded Device Testing – Evaluate firmware, insecure protocols, and physical access risks.
- API & CI/CD Pipeline Testing – Ensure secure authentication, token handling, and pipeline access.
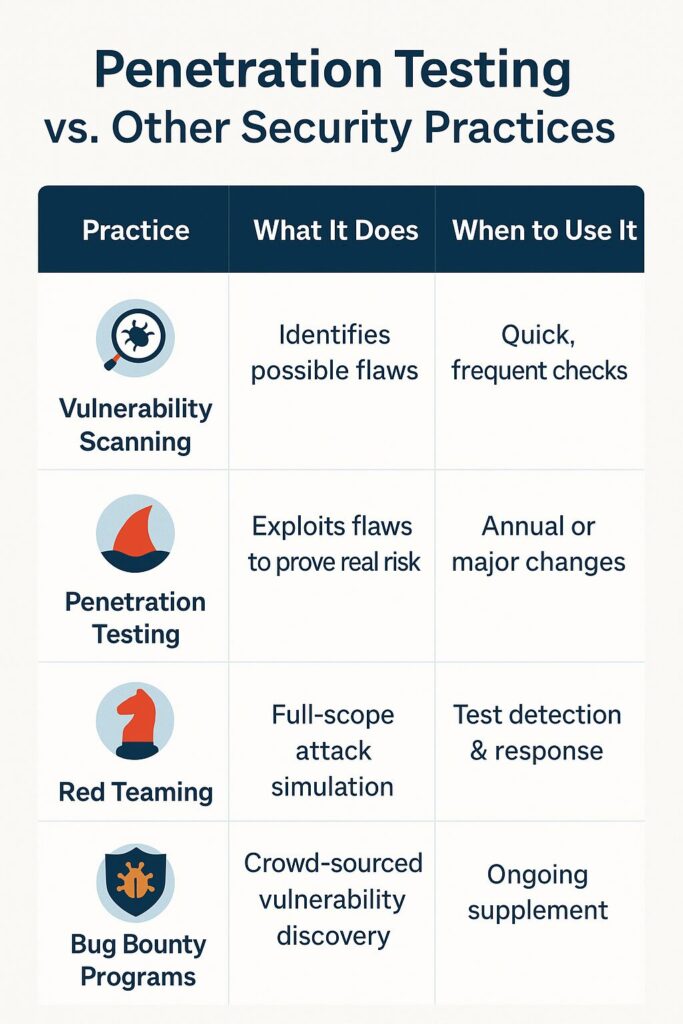
Penetration Testing vs. Other Security Practices
| Practice | What It Does | When to Use It |
| Vulnerability Scanning | Identifies possible flaws | Quick, frequent checks |
| Penetration Testing | Exploits flaws to prove real risk | Annual or major changes |
| Red Teaming | Full-scope attack simulation | Test detection & response |
| Bug Bounty Programs | Crowd-sourced vulnerability discovery | Ongoing supplement |
👉 Penetration testing is the bridge between automated scans and full-scale adversarial simulations.
Real-World Example
A mid-sized e-commerce company ran a web application penetration test before a holiday season launch. The test uncovered:
- SQL injection vulnerabilities in the checkout process
- Misconfigured firewall rules allowing unauthorized traffic
- Weak API authentication tokens in the mobile app
After remediation, the company avoided potential data leaks and built stronger trust with its customers.
Compliance and Regulatory Drivers
Penetration testing is often not optional. Examples include:
- PCI DSS – Annual testing for organizations handling credit cards.
- HIPAA – Security assessments for healthcare data.
- ISO 27001 – Continuous risk assessments.
- SOC 2 – Testing helps demonstrate strong security controls.
Challenges of Penetration Testing
- Cost – Tests can range from $5,000 to $100,000+, depending on scope.
- Time – Most tests take 1–3 weeks, with additional time for remediation.
- Overwhelm – Reports can contain dozens of issues—prioritization is key.
- Executive buy-in – Without leadership support, findings may be ignored.
Future Trends in Penetration Testing
- AI-driven testing – Machine learning to identify vulnerabilities faster.
- DevSecOps integration – Security tests embedded into CI/CD pipelines.
- Continuous penetration testing – Ongoing monitoring instead of annual checkups.
- Cloud-native testing – Specialized tests for Kubernetes, containers, and multi-cloud environments.
Practical Checklist: Preparing for a Penetration Test
- ✅ Define clear scope and objectives
- ✅ Obtain executive approval
- ✅ Back up critical systems
- ✅ Communicate with IT and stakeholders
- ✅ Plan for remediation before the test begins
FAQs About Penetration Testing
How often should penetration testing be done?
At least annually, and after significant system changes.
Can penetration testing disrupt business operations?
When scoped properly, tests are safe and designed to minimize impact.
Is pen testing only for large organizations?
No. Small businesses are often targeted precisely because they lack testing.
What certifications should penetration testers hold?
Common ones include OSCP, CEH, and GPEN.
Key Takeaways
- Penetration testing simulates real-world cyberattacks to uncover exploitable weaknesses.
- It’s essential for compliance, risk reduction, and customer trust.
- The process involves planning, scanning, exploitation, reporting, and retesting.
- Tests should cover networks, web apps, mobile apps, cloud environments, APIs, databases, IoT, and CI/CD pipelines.
- Unlike vulnerability scans, pen tests prove real-world risk impact.
- Future trends include AI-driven testing and continuous monitoring.
Final Thought
Penetration testing is not just about ticking a compliance box—it’s about building confidence in your security posture. Ask yourself:
If hackers tested your systems tomorrow, would you pass the test?
Now is the time to find out—on your terms.